For all of you YouTubers out there, you probably already know that the video-playback website is offering a premium service that launched last month. Now you can watch cat videos and other nonsense in an entirely new way. But what do you get with a subscription to YouTube Red? Is it worth the money? Well, let’s find out.
Network Synergy Blog
Network Synergy has been serving the Trumbull area since 1988, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
0 Comments
With the Internet of Things continuing to gain popularity, we’re seeing more devices that connect to the Internet than ever before. However, what the users of these devices might be failing to take into consideration is the fact that the Internet is a dangerous place full of threats and other miscreants. What happens if these criminals decide to attack any of your connected devices? This is a relevant question to ask since October is Cyber Security Month, and The Internet of Things represents the next frontier of cyberspace.
Have you ever wondered how your PC is identified from the billions of devices out there in the world today? Just like every human being has specific physiological traits that make up who they are, your computer’s IP address is somewhat unique to your machine, and it can say a lot about you. Therefore, it’s important that you are able to identify your own IP address when you need to.
A business’s website is one of its lifelines; it can either make or break your online presence. One of the most important parts of having a website, though, is owning your domain name. There are a lot of different choices for them, but do you know that at one point in history, they had their own individual uses and meanings?
As a business owner, you might have the sudden and inexplicable urge to creep on (track) your competitors to get a feel for their prices and services. With these six apps, you can make this job a little bit easier by seeing what others have to say about your competitors, including what they are saying about you.
We all know how annoying WiFi can be at times. Sometimes it’s simply a bad connection, or perhaps there are too many devices accessing your network. Or, maybe it’s your sneaky neighbor stealing your WiFi. Regardless of what the cause is, there’s a way to check your WiFi usage in the Windows operating system.
When the Internet was first established, malware and hacking were in their infancy, and not as much of an immediate problem as they are today. Thanks to this fact, the Internet wasn’t really created with a certain security design in mind, and has instead adapted to shifts in its environment. Unfortunately, as hackers grow more powerful, several of these patchwork protocols are growing outdated.
The Internet of Things is changing the face of web-connected devices as we know it. Some would argue that the world isn’t ready for the IoT, but it’s on its way nonetheless. But what really constitutes the Internet of Things? InfoWorld suggests that a lot of what the public sees as the Internet of Things shouldn’t be classified as IoT devices. Therefore, we need a more substantial definition for this revolutionary phenomenon.
Major retailers are having a rough time of it these days concerning the security of their customer's financial information. Last December, Target was hit with malware that compromised 40 million customer credit and debit card accounts, and recently, Home Depot was hit with the same malware. What's a connoisseur of mass-produced boxed goods to do?
In Europe, there's a lot of discussion about whether or not citizens have the right to be forgotten, or rather, be forgotten by search engines. According to a May 2014 ruling, search engines must consider requests from the public for removal of content. Not just any content, though; according to ZDNet, the content must be "inadequate, irrelevant, or no longer relevant." As you might guess, this concept is extremely controversial.
Does your company have dedicated antivirus software to protect it against the annoying threats on the Internet? Sometimes, a computer virus can weasel its way past your software, but there's no greater frustration than when you realize that the reason you contracted a virus is because an employee disabled your software. Don't let this happen to you!
We all know about the cryptocurrency Bitcoin, but do you know about Dogecoin? Its figurehead, the grammatically-challenged Shiba Inu, quickly became an Internet sensation called the Doge meme, and was adopted as the mascot for Dogecoin. However, before you go out and buy yourself some Dogecoin for you and your buddies, you should know that its database, the Doge Vault, has been hacked.
Can you tell the difference between the two words, Internet and Intranet? The difference is much more than simply two letters. Both are valuable marketing tools, particularly for small businesses, but what exactly differentiates them from each other? The key to understanding this is a simple English lesson.
19 years ago, a class of fifth graders from Helena, Montana was featured in a PSA video that, looking back, made some eerily-close predictions about how the Internet is used today. When this PSA was shot in 1995, only 0.4% of the world's population regularly used the Internet. Today, nearly 39% of the world uses it, and for good reason, as predicted all those years ago.
We've all wasted time surfing the Internet, but as we know, there are unfortunately extremes to every action. Wasting time by mindlessly browsing Internet pages can certainly become a problem when it claims huge portions of your time at work, killing your productivity. Can you not seem to get away from surfing the Internet?
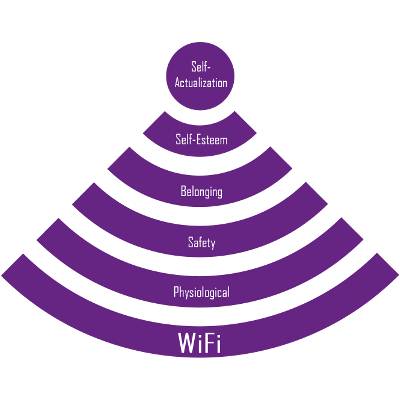
In 1943, psychologist Abraham Maslow published a paper about human motivation that would become the well-known Maslow's Hierarchy of Needs. His theory states that before self-actualization can be achieved, four needs must first be met, like esteem, belonging, safety, and physiological (the most basic which includes, air, food, water, etc.). In 2014, we feel the need to add one more layer to Maslow's pyramid: WiFi.